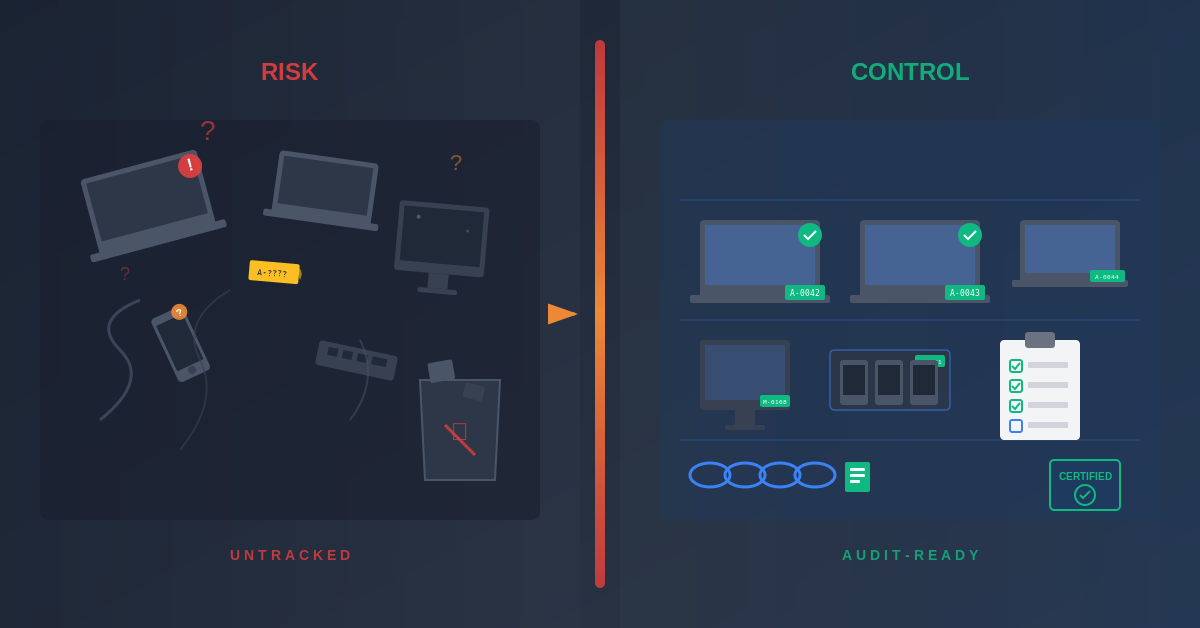
Laptops walk out of the office and never return. Monitors pile up in storage closets. And if you’re lucky, someone’s still keeping a spreadsheet of serial numbers.
Unlike centralized data centers, end-user IT equipment is scattered, inconsistently tracked, and often overlooked when it’s time for decommissioning. That’s where the risk starts—and where most organizations lose money, data, and compliance credibility.
These aren’t just “old computers.” They’re portals to customer data, employee records, financial files, and intellectual property. If you’re not handling device retirement with airtight protocols, you’re leaving doors open to security breaches and regulatory violations.
Key factors that complicate asset disposition for end-user devices:
- Decentralized ownership – Devices used remotely or across departments aren’t always reported back to IT.
- Shadow IT and “Bring Your Own Device” overlap – It’s not always clear who owns what, or where the data ends up.
- Inconsistent tracking and inventory management – Serial numbers, wipe confirmations, and usage logs get lost over time.
- DIY disposal or recycling shortcuts – Well-meaning staff toss devices in e-waste bins without proper, secure data destruction or resale recovery.
It’s a blind spot, and one with real consequences. But it’s an opportunity when managed by a certified ITAD Service company.
Have questions about our ITAD services and process, or just want to learn more about your options? Click here >>
Why Corporate End-User Devices Pose Unique Disposition Risks
When enterprise IT leaders hear “hardware retirement,” they’re often thinking about servers or data centers. But the real risk — and the real volume — is sitting on desks, in remote offices, or still in someone’s backpack.
Corporate end-user devices include:
- Laptops and desktops
- Monitors and docking stations
- Keyboards, mice, printers, and peripherals
- Mobile devices and tablets
The problem? These devices are decentralized, harder to track, and often missed in company-wide IT asset disposition (ITAD) plans. That means more gaps in your chain of custody and more opportunities for data leaks, noncompliance fines, and brand damage.
Common scenarios that multiply risk:
- Devices issued to remote workers never get returned
- Retired laptops dumped in “e-waste bins” with no tracking
- Wiped hard drives that weren’t actually wiped (hello, data remnants)
- Inconsistent documentation for audit purposes
Without a formal recovery process for these devices, your company’s security posture isn’t just weakened, it’s exposed.
Checklist: Proper Retirement of Laptops, Desktops, and Monitors
If you’re in charge of retiring end-user devices—whether you’re an IT director managing 500 endpoints or a purchasing manager cleaning out storage closets—you already know the stakes are high. Data risk, inventory bloat, and compliance issues don’t magically vanish when a laptop goes offline.
Here’s what needs to happen before that device leaves your custody:
1. Asset Inventory & Validation
Track everything—make, model, serial number, asset tag. You can’t manage what you can’t see. Spreadsheets and sticky notes don’t cut it anymore. Use a system (or partner with one) that validates inventory against your master list. Especially important in remote/hybrid setups where devices are spread across cities, or even countries.
2. Data Sanitization (with Audit Trail)
This step isn’t optional—and no, deleting files isn’t enough.
Wipe every drive using a method that meets NIST 800-88 or DoD 5220.22-M standards. Better yet, use Blancco-certified wipes for automatic proof-of-wipe documentation. If the drive can’t be wiped, go physical: degaussing, shredding, or crushing.
And keep your receipts. You’ll want serial-matched logs in case an auditor (or attorney) ever asks.
3. Chain of Custody Tracking
As soon as the device leaves your location, your liability doesn’t end—it evolves.
You need a clear, documented chain of custody: who picked it up, where it’s going, how it’s transported, and what happens when it gets there. This is especially crucial when working with third-party ITAD providers.
4. Environmental Compliance & Certifications
Old monitors can be loaded with mercury. Desktops? Leaded solder and batteries. You can’t just toss this stuff in a bin labeled “e-waste.”
Use an ITAD provider with R2v3 or e-Stewards certification. That’s your guarantee that downstream recycling is done responsibly and legally.
5. Value Recovery or Donation Path
Even at end-of-life, most corporate laptops and desktops still hold resale or refurb value. If data destruction was handled properly, you can offset costs—or donate gear to qualified organizations.
Ask your provider about buyback options or refurb pathways that align with your compliance policies.
6. Final Certificate of Disposition
This is your proof. It should include:
- Serial numbers
- Wipe method used (if applicable)
- Destruction method (if physical)
- Date and location of processing
- Name of technician or automation log
Don’t accept vague receipts or summaries. If your internal compliance officer or legal team wouldn’t sign off on it, neither should you.
Want to skip the guesswork?
OEM Connect’s certified ITAD solutions handle all of this—from serialized pickup through data destruction and audit-ready documentation—so you don’t have to lose sleep over what’s sitting in that IT closet.
Let’s talk about your next device retirement cycle. Reach out here.
Frequently Asked Questions About ITAD for Corporate Devices
What qualifies as a corporate end-user device in ITAD?
Corporate end-user devices include any hardware issued directly to employees for day-to-day use. This typically covers:
- Laptops
- Desktops
- Monitors
- Docking stations
- Keyboards, mice, and other peripheralsDevices used in remote, hybrid, or field environments should also be included in your end-of-life ITAD plans.
Why is secure data destruction critical for retiring laptops and desktops?
End-user devices often contain locally stored files, cached credentials, or synced cloud data. If these devices aren’t properly wiped or destroyed, they can pose serious data breach risks—especially if they were used by executives or team members handling sensitive client, financial, or healthcare data.
What is Blancco and how does it help with ITAD?
Blancco is a trusted data erasure software that meets global standards for certified data wiping, including NIST 800-88. When a device is wiped using Blancco, it produces a verifiable audit report showing that the data was fully removed in a secure, compliant manner.
Are Blancco-certified wipes considered R2v3 or e-Stewards compliant?
Blancco itself is not a certification like R2v3 or e-Stewards. However, Blancco-certified wiping is often part of the required process used by recyclers who are R2v3 or e-Stewards certified. OEM Connect, for example, uses Blancco-certified software as part of its full-service, standards-aligned ITAD workflows.
What is chain of custody in IT asset disposition?
Chain of custody refers to the documented trail that tracks each asset from the moment it leaves your organization to its final disposition—whether resale, recycling, or destruction. A reliable ITAD provider will maintain detailed records at every handoff to ensure compliance, security, and peace of mind.
Can I resell corporate laptops and monitors instead of recycling them?
Yes, in many cases, gently used corporate hardware still has resale value. OEM Connect evaluates the condition, age, and specs of your end-user devices and offers a buyback option—reducing waste and recovering value while still providing certified data destruction.
What paperwork should I expect from a professional ITAD service?
You should receive:
- A serialized asset report
- Certificates of data destruction
- Chain of custody documentation
An audit-ready summary for compliance reviews
These documents are critical for IT teams, procurement, and legal departments managing risk and maintaining regulatory alignment.