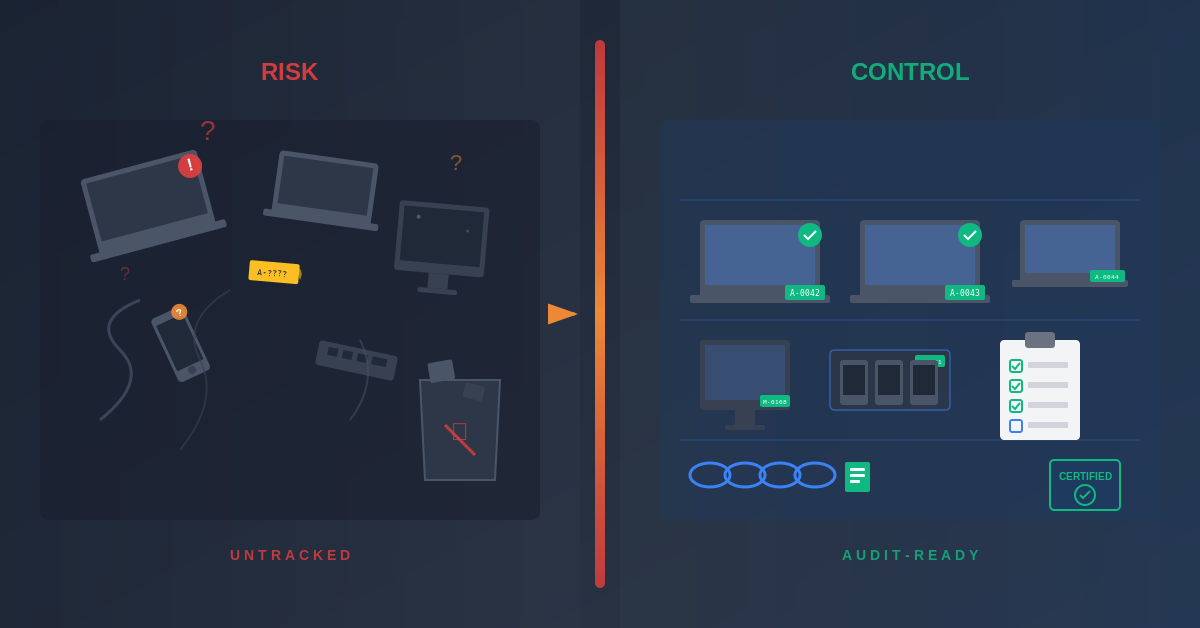
A bank refreshes endpoints on a schedule. But retirement rarely runs on a schedule.
Devices drift into closets, branch storage rooms, remote-worker home offices, and “temporary” piles that quietly become permanent. The result is a double-loss: risk exposure plus missed recovery value.
Most banks treat IT asset disposition as a cost center and a messy afterthought. That’s backwards. To run effective ITAD solutions for banks, it’s two things at the same time: a risk-control workflow and a budget-offset engine.
Quick Answers for Bank ITAD Programs
What bank-grade ITAD actually means before the regulatory deep dive.
What bank-grade ITAD actually means
Verifiable proof of data destruction, unbroken chain of custody, and documented final disposition for every device.
Why endpoints are the hard part
Distributed across branches and home offices with inconsistent tracking and accountability gaps.
How buyback changes the budget conversation
Device value recovery offsets refresh costs instead of generating another disposal invoice.
For busy humans: If it isn’t provable, it doesn’t exist. Banks need serial-matched proof, not informal “we took care of it” summaries.
Why ITAD Solutions for Banks is Different (It’s Not Just “Disposal”)
Banks are documentation-heavy by nature. If it isn’t provable, it doesn’t exist.
Endpoints hold customer data pathways: cached credentials, synced folders, saved files, browser sessions. A laptop that sat in a relationship manager’s office for three years has touched account information, even if nothing was “supposed” to be saved locally. That makes every device a potential exposure point.
“We wiped it” is meaningless without evidence tied to the actual device identity. Banks need serial-matched proof, not informal internal habits or summary statements that cover 200 devices with one generic certificate.
Secure data destruction means verifiable, auditable sanitization aligned to NIST methods and documentation, not a technician running a delete command and calling it done.
The Two Outcomes Banks Actually Need: Risk Closure and Cost Offsets
Most ITAD solutions for banks articles stop at security. Banks also need the CFO and procurement story.
Risk closure requires three elements:
Serial-matched proof that data is gone, tied to the specific device that left your custody. Chain-of-custody continuity showing every handoff from decommission to final disposition. Final disposition evidence documenting whether each device was reused, resold, recycled, or destroyed.
Budget offsets change how finance views refresh cycles:
A reuse-first approach to IT asset recovery preserves device value when drives pass certified sanitization. Value recovery through buyback reduces the net cost of refresh cycles, turning disposal from a pure expense into a partially self-funding operation.
Here’s the key insight most banks miss: you don’t need a “vendor.” You need a repeatable retirement lane that produces control evidence every single time, regardless of which branch initiates the retirement or which employee is off-boarding.
Where Bank Endpoint ITAD Programs Break (Multi-Site and Remote Workers)
The failure modes are predictable and vivid:
Branch-to-branch inconsistency means this region does it one way, that region does it another. IT knows the policy exists but can’t explain why compliance isn’t happening everywhere.
Remote worker retrieval gaps create offboarding drift. An employee leaves, ships their laptop back (maybe), but the monitor and dock stay in their home office for six months. Or forever.
Monitors, docks, and peripherals get treated as “not risky” and skipped entirely, even though many contain firmware and local storage.
Shadow disposals happen when well-meaning teams donate or recycle devices without proof, thinking they’re being helpful. They are not.
End-user devices are decentralized and often overlooked compared to centralized data center equipment. That decentralization is exactly what makes endpoint ITAD the harder operational challenge.
A Bank-Grade Endpoint ITAD Workflow (Simple Enough to Repeat)
The workflow needs to be non-negotiable but practical. Here’s what that looks like:
Intake and inventory standardization starts with minimum required fields: asset tag, serial number, user or location assignment, device type, and condition class. “Unknown devices” get quarantined into the same process, not ignored or treated as exceptions.
Retrieval designed for real life accounts for multi-site pickups across branch networks, remote return kits with shipping instructions and actual deadlines, and consolidation logic so you’re not shipping air in half-empty boxes.
Data handling with proof means sanitization methods aligned to recognized guidance like NIST 800-88 media sanitization standards. Certificate output must match device serials. No “batch summary” hand-waving that claims 47 devices were processed but doesn’t specify which ones or how.
Triage for recovery versus destruction grades devices for resale, refurbishment, or buyback potential. Devices that fail sanitization or have damaged drives escalate to physical destruction. You don’t “hope it wiped.”
Closeout reporting delivers an audit packet to procurement and compliance with an exception log documenting lost-in-transit items, physically damaged devices, or drives with unreadable sectors, plus resolutions for each.
Banks commonly lean on NIST media sanitization guidance as a defensible baseline for data sanitization approaches. Regulators and bank examiners emphasize controls around operations, including end-of-life handling and disposal of data and media within IT operations guidance.
Vendor Checklist for ITAD Solutions for Banks
Use this as a fast filter when evaluating partners:
Can you produce serial-matched wipe or destroy reports? Banks don’t pass audits on vibes. You need proof tied to the exact asset, not a summary that could describe anyone’s devices.
Can you prove chain of custody end-to-end? Every handoff is a risk point, especially across branches and third-party carriers. If custody documentation has gaps, you have gaps in defensibility.
Are you aligned with the right standards and certifications? Don’t overpromise. Specify what matters for the bank’s policy and region (R2v3, e-Stewards, ISO certifications as applicable).
What’s your triage and grading process for value recovery? If everything gets shredded, your “budget offset” story dies. Ask how they determine what can be sanitized and resold versus what must be destroyed.
How do you handle remote returns and multi-site pickups? This is where programs actually fail in the real world. Generic “we do pickups” isn’t specific enough.
How do you prevent lost assets in transit? Labels, tracking systems, packaging rules, escalation SLAs, and exception reporting. Lost devices are audit findings waiting to happen.
What does your audit packet look like? If they can’t show a sample packet on request, that’s your answer. Walk away.
Support the “certificate/proof” logic with certified ITAD and documentation emphasis.
Common Failure Modes That Blow Up Bank Endpoint ITAD
These failure modes show up in audit findings and compliance reviews:
“We recycled it” with no serialized reporting. You have no proof the device ever reached the recycler, much less what happened to it.
“We wiped it” with no proof tied to the device. Internal IT wiping devices before retirement creates zero defensible evidence for auditors.
Shadow disposals where departments donate or trash devices without involving IT or compliance. Good intentions, catastrophic documentation gaps.
Backlog closets becoming permanent storage. Risk accumulates and device value evaporates while everyone assumes someone else will deal with it eventually.
Inconsistent policies across sites turn branches into exception factories. Policy exists centrally but implementation varies wildly by region.
Operational guidance from regulators expects disciplined end-of-life handling, not improvisation or “we’ll figure it out per situation” approaches.
How to Talk About This Internally (So It Gets Funded)
Different stakeholders need different value propositions:
Procurement gets predictable program costs with fewer emergency shipments and last-minute vendor scrambles. Budget forecasting improves when retirement runs on process, not crisis.
Compliance receives consistent evidence trails that survive audits. Exception handling is documented, not buried or ignored.
IT deals with fewer side quests and urgent requests to “find proof we destroyed something two years ago.” Standardization reduces operational drag.
Finance sees recovery value offsetting refresh costs. Instead of budgeting the full replacement cost, you budget net cost after value recovery, which changes refresh cycle economics.
Position ITAD as an operational control that also generates budget offsets. That dual benefit gets attention from both risk and finance leadership.
Want a Clean Retirement Lane (and a Sample Audit Packet)? Click here >>
Frequently Asked Questions: ITAD for Banks and Financial Institutions
Straight answers for bank IT, compliance teams, and procurement leaders navigating endpoint disposition across branches and remote workers.
What regulations govern ITAD for banks and financial institutions?
Banks operate under multiple overlapping data protection frameworks. The Gramm-Leach-Bliley Act (GLBA) requires financial institutions to safeguard customer information throughout its lifecycle, including during disposal. Sarbanes-Oxley (SOX) imposes strict controls on how financial data is handled and retired. The Payment Card Industry Data Security Standard (PCI DSS) mandates secure disposal of any equipment that processed cardholder data. The Dodd-Frank Act requires transparency in how sensitive data is destroyed, and the FTC Disposal Rule mandates that covered institutions maintain systems for secure information disposal. Banks commonly lean on NIST 800-88 media sanitization guidance as a defensible baseline, and the FFIEC emphasizes operational controls around end-of-life handling within IT operations guidance. The key takeaway is that banks need documented, repeatable processes with proof of compliance, not informal disposal habits.
What happens if a bank fails to properly dispose of IT assets?
The consequences are severe and measurable. In 2022, Morgan Stanley agreed to a $35 million SEC settlement after the firm hired a moving company with no data destruction expertise to decommission thousands of devices containing customer PII. The settlement covered failures affecting approximately 15 million customers. Beyond direct fines, banks face mandatory breach notification costs, regulatory examinations, remediation expenses, and reputational damage that erodes customer trust. Legal liabilities can include class action lawsuits and compensation claims. Failed ITAD doesn’t just create a compliance gap, it creates an existential risk to the institution’s operating permissions and market position. Regulators view improper disposal as evidence of broader control weaknesses, which triggers deeper scrutiny across all operations.
Do banks need to use ITAD vendors with special certifications?
Yes, and those certifications provide the audit trail banks need to demonstrate due diligence. R2v3 (Responsible Recycling) certification verifies responsible downstream processing and environmental compliance. NAID AAA certification specifically addresses data destruction operational security and demonstrates independent auditing of destruction processes. e-Stewards certification ensures environmental responsibility throughout the recycling chain. ISO 9001, 14001, and 45001 certifications cover quality management, environmental management, and occupational health and safety. Banks should verify that vendors hold the relevant certifications for your jurisdiction and risk profile before engagement. A vendor without these certifications cannot provide the documentation rigor that survives regulatory examination. If a vendor can’t prove their processes are independently audited, that tells you everything you need to know about working with them.
What is ITAD and how does the IT asset disposition process work?
IT Asset Disposition (ITAD) is the secure and environmentally responsible process of retiring IT equipment at end-of-life. For banks, it’s both a risk-control workflow and a budget-offset engine. The process starts with asset intake and inventory standardization, capturing minimum required fields like asset tag, serial nu