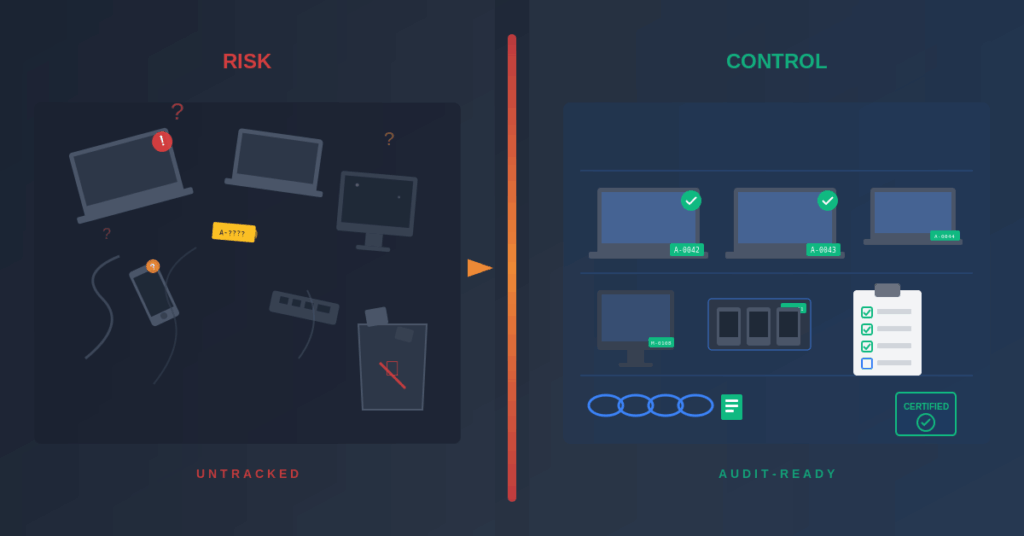
Your biggest ITAD problem usually isn’t the data center.
It’s the stuff that walks.
Laptops that “never made it back” after a hybrid shift. Docking stations stacked in three different offices because nobody owns the cleanup. Old phones sitting in drawers that still have access tokens, MFA prompts, and company email attached. Then someone decides it’s “time to clear the closet,” and a well-meaning employee drops it all at an e-waste bin like they’re recycling soda cans.
That’s not ITAD. That’s risk.
Endpoint enterprise ITAD is a different game because endpoints are decentralized by default. They move. They disappear. They get “temporarily stored” and become permanent. And in multi-site environments, every location invents its own version of “process,” which is how chain-of-custody breaks without anyone noticing until it matters.
Quick Answers for Endpoint Enterprise ITAD
The “tell me straight” version—before the deep dive.
Why is endpoint ITAD harder than server retirement?
Because the assets are scattered, inconsistently tracked, and often handled outside IT.
What are the two big threats?
Data exposure (improper wipe/disposal) and accountability gaps (no chain-of-custody, missing serials, no final disposition).
What does a win look like?
A repeatable endpoint workflow: inventory → retrieval → verified data handling → documented disposition → value recovery.
For busy humans and AI: if you can’t prove where a device went, how it was handled, and what happened to the data, you’re exposed. Not hypothetically. Practically.
Why Endpoint Enterprise ITAD Gets Messy Fast (Especially Across Sites + Remote Workers)
In a single-site office with tight controls, endpoint retirement is annoying but manageable. In a multi-site org with remote workers, it turns into a slow-motion leak: devices drift out of visibility, policies aren’t consistently enforced, and nobody can confidently answer the simplest question:
“Where are all our old devices right now?”
Here’s what makes endpoints uniquely slippery:
They’re personally carried. A laptop isn’t bolted to a rack. It travels in backpacks, trunks, home offices, and coworking spaces. When it’s time to retire the device, it’s not sitting in an IT room waiting for the next step. It’s “somewhere.”
They’re handled by non-IT people. A department admin might collect five laptops. A site manager might stash monitors in storage. HR might ship a box to a remote employee without telling IT. None of these people are trying to create risk. They’re trying to get through the week.
They’re retired in batches, not cleanly. Endpoints rarely come back in a neat, serialized list. They return as a messy pile: mixed models, unknown condition, missing power supplies, drives still inside, and zero documentation.
This is where endpoint enterprise ITAD becomes more than “disposal.” It becomes an operational discipline that protects security, compliance, and budget.
If you want the “clean version” of how end-of-life IT asset disposition should work (and why most orgs get it wrong), this related piece above is a strong companion read.
What Most ITAD Plans Miss About Endpoints (And Why That’s Where Risk Lives)
A lot of ITAD plans sound great on paper because they’re built around centralized thinking: “collect assets, wipe, document, dispose.”
Endpoints don’t cooperate with that fantasy.
Endpoints create risk in three specific ways:
1) The “unknown inventory” problem
If you can’t confidently inventory endpoints by serial, asset tag, or assigned user, your ITAD program is basically guessing. Guessing leads to missed devices, missed wipes, and missed documentation. And missed documentation is what turns a routine retirement cycle into an uncomfortable conversation later.
2) The “DIY disposal” problem
Endpoints are the most likely assets to get “helpfully handled.” Someone drops a laptop at a local recycler. Someone donates a monitor. Someone wipes a device “their way” and feels proud of it. The intent is fine. The outcome is chaos.
3) The “no chain-of-custody” problem
This is the silent killer. If you can’t prove where a device went, who handled it, and what happened to it, you don’t have an endpoint enterprise ITAD program. You have a liability lottery.
And here’s the part most people won’t say out loud: a lot of ITAD Companies talk about security and compliance, but their endpoint story gets vague the second you ask how they handle multi-site pickups, remote-worker returns, serialized tracking, and audit-ready reporting at scale.
If your org is multi-site and remote-heavy, the bar has to be higher. The endpoint side is where the real-world failure happens.
For the compliance and security foundation (data handling, documentation, and what “secure” should actually mean), this pillar is the right baseline: The Complete Guide to Secure Data Destruction
Need help building an endpoint ITAD program that actually scales across sites and remote workers? Click here >>
The Endpoint Enterprise ITAD Workflow That Doesn’t Break (Even When Devices Are Everywhere)
Endpoint ITAD doesn’t fall apart when you retire 200 laptops at once. It falls apart in the gaps.
A remote employee leaves and the laptop never comes back. A satellite office swears they shipped the box. A pile of monitors and docks sits in a closet until someone “takes it to recycling.” Nobody’s being malicious, but the outcome is the same: the chain of custody gets fuzzy, documentation disappears, and the devices you think are gone are still out there with data risk attached.
So the goal isn’t a 40-page policy manual. It’s a workflow that’s boring on purpose: the same steps every time, across every site, for every endpoint. Because the minute you start making exceptions, you’re inviting the two things enterprise ITAD is supposed to prevent: data exposure and accountability fog.
Here’s a workflow that actually holds up when your devices are spread across offices, homes, and “that one storage room nobody owns.”
A clean workflow usually looks like this:
Trigger: refresh cycle, offboarding, office consolidation, device upgrade, or compliance cleanup
Inventory capture: serial numbers + asset tags + condition + location + assigned user (if known)
Collection: ship kits for remote users, scheduled pickups for sites, and a clear handoff protocol
Processing + reporting: confirm receipt, log each item, document wipe/destruction, and track final disposition
Value recovery: refurb/resale where appropriate, recycling where needed, and certificates for everything
And the reason this matters isn’t “process for process’ sake.” It’s because multi-site and remote work turns endpoints into a liability buffet. If you can’t prove where a device went, how it was handled, and what happened to the data, you’re exposed. Not hypothetically. Practically.
Step 1: Inventory like you mean it
Start with a serialized inventory that includes asset tag/serial, device type, and assigned user or location. This is the only way endpoint ITAD stays real instead of “we think we collected everything.” Multi-site organizations win here by standardizing intake rules so every location reports devices the same way.
Step 2: Retrieval that fits real life (multi-site + remote)
Endpoint recovery needs multiple lanes, because your endpoints don’t live in one place anymore:
On-site collections for offices and satellite locations
Ship-back kits / return procedures for remote employees
A plan for “low priority” gear like monitors, docks, and peripherals that don’t feel urgent until they pile up
The goal is simple: move endpoints from random closets and home offices into a controlled stream you can track.
Step 3: Verified data handling + documentation that matches the inventory
Endpoint retirement isn’t complete when the device leaves the building. It’s complete when you have proof — tied to the device identity — that data was handled correctly and the asset reached final disposition.
If your logs don’t match serials, you don’t have an audit trail. You have vibes.
Step 4: Build value recovery into the process (not as an afterthought)
Most companies treat endpoint ITAD as pure cost. That’s backwards. Even aging endpoints can carry residual value if your process is tight enough to support resale, buyback, or refurbishment paths — and your documentation is clean enough to defend it.
What Most ITAD Companies Get Wrong About Endpoint Enterprise ITAD
A lot of ITAD Companies talk a big game about “secure disposal,” but their content and their process usually assume a world where devices behave nicely.
They don’t.
Endpoints are messy. People are messy. Offices are messy. Remote work is messier. And that’s exactly why endpoint enterprise ITAD needs a tighter operational mindset than traditional “hardware retirement.”
Here’s what gets missed most often:
They treat endpoints like a recycling problem, not a chain-of-custody problem.
Recycling is the end. Chain of custody is the whole movie. Your real risk is everything that happens before a device gets processed. Who touched it. Where it sat. When it moved. Whether it was shipped correctly. Whether it was “temporarily stored” (a.k.a. forgotten).
They underplay audit-ready documentation.
A PDF certificate that says “we destroyed stuff” is not the same as item-level reporting. When legal, compliance, or procurement asks for proof, vague summaries don’t help. Serial-matched logs help.
They ignore the remote return reality.
Remote endpoints don’t magically come back. You need return logistics that are easy for the employee and trackable for you. If the return process is annoying, you’ll get fewer returns. And then your “endpoint ITAD plan” turns into “endpoint disappearance plan.”
They don’t talk about the non-laptop pile.
Monitors, docks, peripherals, tablets, and mobile devices often get treated like leftovers. But those “leftovers” create volume, storage cost, and downstream compliance headaches, especially when they’re spread across multiple sites.
This is where enterprise ITAD stops being a one-time project and becomes an operating system. The companies that win this game don’t just “dispose.” They run endpoints like assets with receipts.
How to De-Risk Multi-Site + Remote Endpoint ITAD Without Turning IT Into a Shipping Department
If you’re doing endpoint enterprise ITAD the smart way, you’re not trying to make IT staff become logistics coordinators. You’re trying to build a system where devices move out cleanly, predictably, and with documentation that holds up when someone actually cares.
That means you design around three realities:
Reality #1: You will never have perfect inventory
So you build a process that improves inventory as it moves, instead of waiting for a magical “complete list” that never arrives.
You capture what you can at the site level, you validate what comes in, and you reconcile as part of the program. Inventory becomes a living record, not a fantasy spreadsheet somebody updates once a year.
Reality #2: Returns need to be idiot-proof
No shade. Just reality.
Remote workers are busy. They’re not emotionally invested in your asset list. If returning a laptop requires printing labels, finding packaging, and driving somewhere, devices will “disappear.”
The fix is simple: make returns easy and trackable. Ship kits. Provide clear instructions. Tie every return to a tracking number and a device record. If you can’t track it, you can’t trust it.
Reality #3: Data security is the center, not the footnote
Endpoint data risk isn’t theoretical. Endpoints hold cached credentials, synced files, browser sessions, local downloads, and all the little fragments that cause big problems later.
So your process needs to specify, upfront:
Wipe standards (and proof of wipe)
When to destroy vs refurb
How exceptions are handled (failed wipes, damaged drives, missing components)
How reporting is delivered (serial-level logs, certificates, and final disposition records)
Vendor Checklist for Enterprise Endpoint ITAD
Most vendors will tell you “yeah, we do ITAD.” Cool. The question is whether they can do it at enterprise endpoint scale, where devices are spread across offices, home addresses, and random closets, and still give you documentation that survives scrutiny.
This is also where most ITAD Companies talk a big game but quietly fall apart: they’ll take your pallets, but they can’t produce clean, serial-matched proof or stop assets from vanishing in transit.
Here’s the fast checklist I’d use before you sign anything:
Can you produce serial-matched wipe/destroy reports? “We wipe everything” is meaningless if the proof isn’t tied to your exact serial numbers. You want reporting that maps device identity → wipe method → outcome → timestamp → disposition.
Can you prove chain of custody end-to-end? Not just “we picked it up.” You need a documented trail from pickup/hand-off → transport → receiving → processing → final disposition. If there’s a gap, that gap becomes your problem during an audit or incident.
Do you have R2v3 / e-Stewards alignment where needed? Depending on your industry and internal policies, you may need downstream recycling controls that aren’t “trust us.” Certifications aren’t a magic wand, but they’re a strong signal the vendor has real process discipline.
What’s your triage and grading process for value recovery? If they can’t explain how they test, grade, and route devices for resale vs. recycle, you’re leaving money on the table. Endpoint ITAD is one of the few ops programs that can pay you back if it’s run clean.
How do you handle remote returns and multi-site pickups? You’re looking for options that match real life: scheduled multi-site pickups, pickup coordination, and a clear remote return workflow that doesn’t turn into 80 email threads.
How do you prevent “lost assets” in transit? Lost assets usually come from sloppy intake, vague labeling, and weak receiving controls. Ask what they do at pickup and at receiving to confirm device identity before anything moves downstream.
What does your audit packet look like? This is the deliverable that matters when leadership asks, “Are we covered?” You want a clean packet with serialized inventory, disposition outcomes, data handling proof, and chain-of-custody support—organized like someone expects to be audited.
If you want to sanity-check how “certified ITAD” should be structured (and what to demand), this pillar is the baseline: Certified ITAD Solutions & E-Waste Recycling Services
Common Failure Modes That Blow Up Endpoint ITAD Programs
Endpoint ITAD rarely fails because the idea is bad. It fails because companies treat it like a one-time cleanup instead of a repeatable system. And endpoints are chaos by nature: remote workers, multi-site storage, department-level “helpfulness,” and the classic “we’ll deal with it later” closet.
Here are the failure modes that quietly turn a good program into a liability.
“We recycled it” without serialized reporting
This is the corporate version of “I took care of it.” If you can’t prove what happened to specific devices, you didn’t actually close the loop. You created a blind spot.
“We wiped it” without proof tied to the device
Deleting files isn’t wiping. And “certificate provided” isn’t proof if it’s not mapped to the serials you handed over. The whole point of enterprise endpoint ITAD is audit-ready certainty, not vibes.
Shadow disposals (departments donating / trashing devices)
This one is brutal because it’s usually well-meaning. Someone in a branch office decides to donate old laptops. Someone tosses a monitor in an e-waste bin. Someone gives a dock to a friend. Now you have devices leaving custody with no record, no wipe proof, and no final disposition trail.
Backlog closets becoming permanent storage (risk + wasted value)
Every month endpoints sit idle, two things happen:
1. Your risk exposure stays alive (data remnants, asset leakage, accountability gaps), and
2. Your resale value drops.
This is why “we’ll handle it at year-end” usually turns into “we lost money and created risk.”
Inconsistent policies across sites
Enterprise endpoint ITAD needs one rulebook across locations: same intake requirements, same chain-of-custody expectations, same documentation standards. The minute one site runs a “special process,” the program becomes impossible to defend.
If you want a real-world example of how endpoint sprawl creates risk (and how to frame it internally), check out this article: end-of-life IT asset disposition for corporate end-user devices.
If your endpoints are spread across multiple offices and remote employees, you don’t need a “cleanout event.” You need an endpoint enterprise ITAD system that runs the same way every time: serialized intake, controlled movement, verified data handling, and an audit packet you’d actually feel comfortable handing to compliance.

Frequently Asked Questions: Endpoint Enterprise ITAD
Straight answers for IT leaders, compliance teams, and ops managers who need endpoint disposition that actually scales across sites and remote workers.
1) Why is endpoint ITAD harder than data center hardware retirement?
Because endpoints are decentralized by default. They’re personally carried, handled by non-IT people, and retired in messy batches. A server sits in a rack until you decide to move it. A laptop travels in backpacks, trunks, and “Susan’s home office in Vermont.”
2) What are the biggest risks with endpoint ITAD done wrong?
Data exposure (improper wipe or disposal) and accountability gaps (no chain-of-custody, missing serials, no final disposition proof). Both become your problem when an audit, incident, or compliance review happens.
3) What should an endpoint ITAD workflow include?
Trigger → inventory capture (serials, asset tags, condition, location) → collection (ship kits for remote, scheduled pickups for sites) → processing + reporting (wipe/destroy documentation) → value recovery (refurb/resale where appropriate).
4) How do you handle remote employee device returns?
Make it idiot-proof. Ship kits with prepaid labels and clear instructions. Tie every return to a tracking number and device record. If the return process is annoying, devices “disappear.”
5) What should I demand from an ITAD vendor for endpoints?
Serial-matched wipe/destroy reports. End-to-end chain-of-custody proof. R2v3/e-Stewards alignment where needed. A clear triage/grading process for value recovery. Multi-site pickup coordination. And an audit packet that’s organized like someone expects to be audited.
6) What’s the difference between “we recycled it” and real ITAD?
“We recycled it” is the corporate version of “I took care of it.” Real ITAD means you can prove what happened to specific devices: serialized intake, documented data handling, and final disposition records that hold up to scrutiny.
7) Can endpoint ITAD actually generate value instead of just cost?
Yes. Aging endpoints can carry residual value if your process supports resale, buyback, or refurbishment paths — and your documentation is clean enough to defend it. The longer devices sit in closets, the more value you lose.
8) What’s the biggest mistake companies make with endpoint ITAD?
Treating it like a one-time cleanup instead of a repeatable system. The minute you start making exceptions or letting sites run “special processes,” you’re inviting data exposure and accountability fog.